Description:
Explore threat modeling methodologies for complex cloud technologies in this LASCON conference talk. Discover the limitations of traditional data flow diagrams when applied to interconnected systems like OpenStack, Linux Containers, and Docker. Learn from three years of threat modeling experience at Rackspace as the speaker shares valuable insights and demonstrates effective techniques for modeling multi-system OpenStack deployments. Gain practical knowledge on creating useful threat models for developers, operations teams, and security professionals. Delve into topics such as inherited risk, lifecycle documentation, and risk assessment in
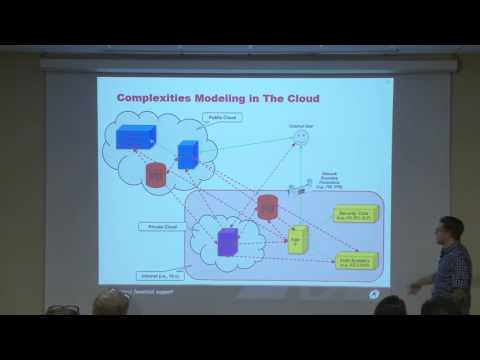
Threat Modeling for Linux Containers LXC, Docker and the Cloud
Add to list
#Conference Talks
#LASCON
#Computer Science
#DevOps
#Docker
#Programming
#Cloud Computing
#OpenStack
#Information Security (InfoSec)
#Cybersecurity
#System Security
#Threat Modeling
#Information Technology
#Virtualization
#Linux Containers