Description:
Discover how to identify and monitor hidden vulnerabilities in your application dependencies in this 27-minute conference talk from Devoxx. Learn about vulnerability indexing systems like NVD and CVE, as well as severity scoring using CVSS. Explore the creation of a Continuous Security pipeline using Jenkins and open-source tools such as OWASP DependencyCheck and DependencyTrack. Gain insights into the DevSecOps philosophy and see practical demonstrations of vulnerability detection, tracking, and mitigation. Cover topics including the National Phenology Database, Heartbleed, common vulnerability scoring, and specific vulnerabilities in popular frameworks like Spring and Jackson. Walk through the process of fixing vulnerabilities, checking base code and dependencies, and implementing security measures using Jenkins plugins, Docker images, and API keys.
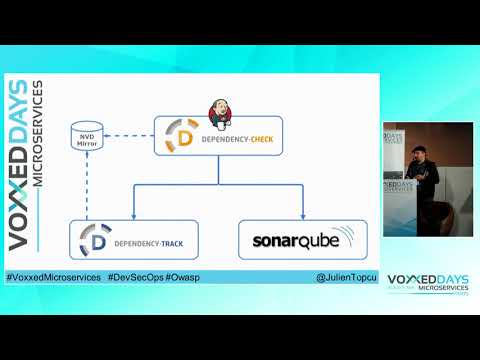
Find and Track the Hidden Vulnerabilities Inside Your Dependencies
Add to list
#Conference Talks
#Devoxx
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#DevOps
#CI/CD
#Jenkins
#DevSecOps
#Vulnerability Management
0:00 / 0:00