Description:
Dive into an extensive 14-hour course on load balancing, proxies, and reverse proxies. Explore the differences between proxy and reverse proxy servers, VPNs, and HTTP proxies. Learn about layer 4 and layer 7 proxying, SSL/TLS termination, and TLS forward proxy. Master popular tools like Varnish, HAProxy, NginX, and Envoy Proxy through comprehensive crash courses. Understand concepts such as fail-over, high-availability, service mesh proxies, and sidecar proxies. Set up active-passive clusters with Keepalived and HAProxy, and compare active-active vs. active-passive cluster architectures. Discover DDOS mitigating reverse proxies, HTTP tunneling, and how to capture and analyze HTTPS traffic. Gain practical knowledge on load balancing RTMP servers, managing timeouts, and utilizing HAProxy Runtime API for backend maintenance. Taught by Hussein Nasser, this course covers a wide range of topics essential for understanding and implementing proxy technologies in modern network architectures.
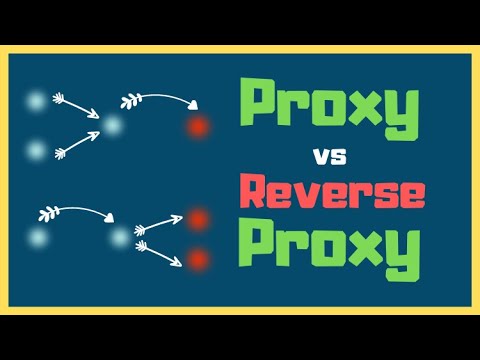
Proxies
Add to list
0:00 / 0:00