Description:
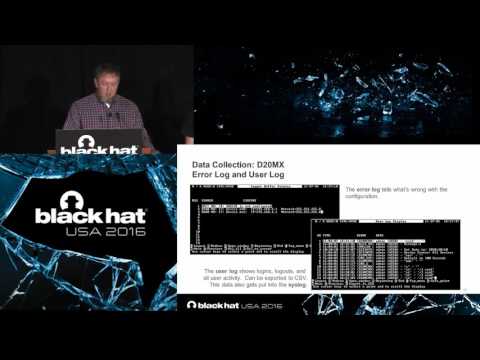
Explore the fundamentals of Digital Forensics and Incident Response (DFIR) for Industrial Control Systems (ICS) in this 25-minute Black Hat conference talk. Delve into the world of embedded devices used in critical infrastructure, focusing on Programmable Logic Controllers (PLCs), Remote Terminal Units (RTUs), and controllers. Learn about the files, firmware, memory dumps, physical conditions, and other data that can be analyzed in embedded systems to determine root causes of compromises or misoperations. Examine practical examples of forensic data collection from two popular RTUs used in Electric Substations: the General Electric D20MX and the Schweitzer Engineering Labs SEL-3530 RTAC. Gain insights into VxWorks, ICS anomalies, forensic evidence gathering, and various shells used in control system devices. Discover techniques for analyzing running configurations, using Wireshark, and performing memory analysis. The talk also covers Windows reverse engineering, cool features, and future plans for ICS DFIR, providing a comprehensive overview of this critical field in cybersecurity.
Read more
What's the DFIRence for ICS?
Add to list
#Conference Talks
#Black Hat
#Programming
#Web Development
#Information Security (InfoSec)
#Digital Forensics
#Reverse Engineering
#Cybersecurity
#Incident Response
#Engineering
#Manufacturing
#Industrial Automation
#Industrial Control Systems
#Electrical Engineering
#Embedded Systems
#Firmware Analysis
0:00 / 0:00