Description:
Explore advanced cryptography concepts in this PHP UK Conference talk. Delve into hash functions, elliptic curves, and quantum cryptography after a brief refresher on secure communication basics. Examine practical applications, including the trustworthiness of web of trust systems and the appropriate use of blockchain technology. Learn about symmetric vs asymmetric encryption, elliptic curve cryptography, key exchange methods, and the SHA2 family of hash functions. Investigate Merkle trees, Bitcoin's underlying technology, blockchain fundamentals, and the factors contributing to Bitcoin's value. Gain insights into cutting-edge cryptographic techniques and their real-world implementations in this comprehensive presentation.
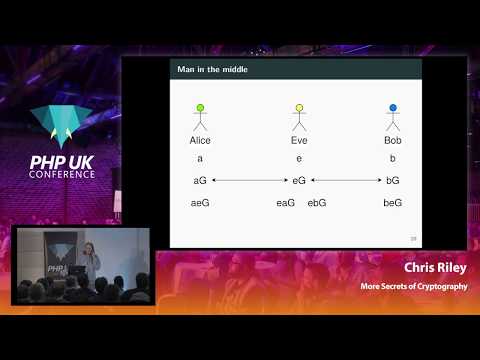
More Secrets of Cryptography
Add to list
#Conference Talks
#PHP UK Conference
#Computer Science
#Cryptography
#Blockchain Development
#Quantum Cryptography
#Hash Functions
#Elliptic Curves
0:00 / 0:00