Description:
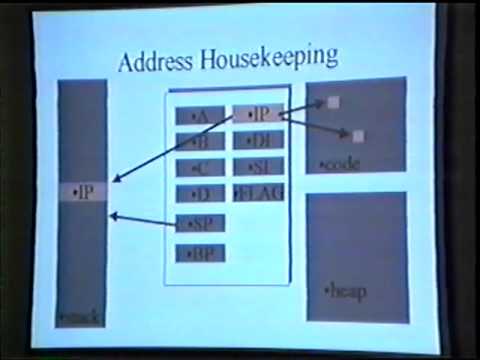
Dive into advanced buffer overflow techniques in this Black Hat USA 2000 conference talk by Greg Hoglund. Explore attack theory, injection vectors, and payload types while learning about the challenges of buffer overflow injection. Examine stack injection techniques, address housekeeping, and endianness considerations. Discover strategies for payload placement, including confined payloads and using more stack space. Investigate HEAP trespassing, VTABLE overwriting, and XOR protection. Compare hardcoded function calls with dynamic function loading, and understand the pros and cons of each approach. Gain insights into HASH loading and CRC checking in this comprehensive exploration of advanced buffer overflow methods.
Advanced Buffer Overflow Techniques
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Cybersecurity
#Ethical Hacking
#Buffer Overflow
#Computer Science
#Data Structures
#Stack Data Structure
#Stack Overflows
0:00 / 0:00