Description:
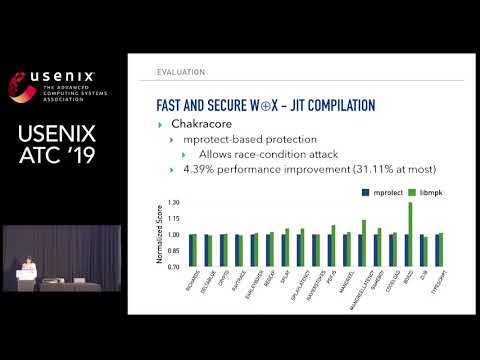
Explore a conference talk from USENIX ATC '19 that delves into libmpk, a software abstraction for Intel Memory Protection Keys (MPK). Learn about the challenges faced by the current hardware implementation and software support of MPK, including security vulnerabilities, scalability limitations, and semantic incompatibilities. Discover how libmpk addresses these issues by virtualizing hardware protection keys, providing access to unlimited virtualized keys, and supporting legacy applications through lazy inter-thread key synchronization. Gain insights into the application of libmpk in real-world scenarios such as OpenSSL, JavaScript JIT compiler, and Memcached for enhanced memory protection and isolation. Understand the performance benefits of libmpk, which introduces minimal overhead compared to unprotected versions and significantly improves performance compared to secure equivalents using mprotect(). The talk covers key concepts including protection-key-use-after-free vulnerabilities, virtualization of protection keys, inter-thread key synchronization, metadata protection, and practical applications in security-critical memory regions.
Read more
Libmpk - Software Abstraction for Intel Memory Protection Keys
Add to list
#Conference Talks
#USENIX Annual Technical Conference
#Computer Science
#Software Engineering
#Scalability
#Information Security (InfoSec)
#Cybersecurity
#Security Vulnerabilities
#Memory Management
#Memory Protection
0:00 / 0:00