Description:
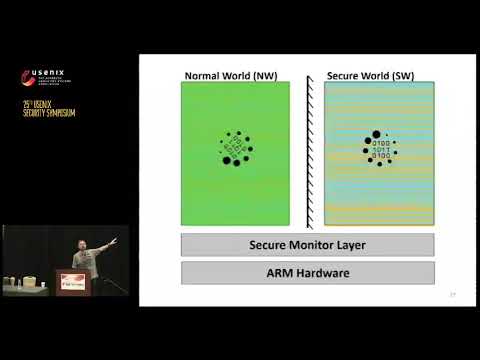
Explore a comprehensive presentation from USENIX Security '16 on fTPM, a software-only implementation of a TPM chip. Delve into the challenges of building trusted systems using commodity CPU architectures like ARM and Intel, and discover how to overcome these obstacles to create software systems with security guarantees comparable to dedicated trusted hardware. Learn about the design and implementation of a firmware-based TPM 2.0 (fTPM) leveraging ARM TrustZone, which serves as the reference implementation for millions of mobile devices. Gain insights into the mechanisms needed for fTPM that can be applied to develop more sophisticated trusted applications. Examine topics such as TPM 1.0 and 2.0, ARM TrustZone properties and limitations, high-level architecture, threat models, and solutions to challenges like long-running commands and dark periods. Conclude with a discussion on SGX limitations and participate in a Q&A session to deepen your understanding of this innovative approach to trusted computing.
Read more
fTPM - A Software-Only Implementation of a TPM Chip
Add to list
#Conference Talks
#USENIX Security
#Information Security (InfoSec)
#Cybersecurity
#System Security
#Threat Modeling
#Engineering
#Electrical Engineering
#Embedded Systems
#Firmware Development
#Computer Science
#Computer Architecture
#ARM Architecture
#ARM TrustZone
0:00 / 0:00