Description:
Explore a comprehensive threat intelligence analysis of the Ukrainian power grid hack in this 43-minute conference talk from BSides Philly 2016. Delve into the Indicators of Compromise, Pyramid of Pain, and tools used in the incident. Examine the ICS Kill Chain, including stages involving Microsoft Office, spearphishing, and the BlackEnergy installer. Investigate the attacker's techniques for stealing files and firmware development. Learn about the Sandworm group, their motivations for targeting Ukraine, and the attack timeline. Discuss similarities with other attacks, potential solutions, and alternative attack vectors. Analyze power grid policies, security gaps, and strategies for improving critical infrastructure protection. Gain valuable insights into cyber threats targeting industrial control systems and the complexities of defending against sophisticated adversaries.
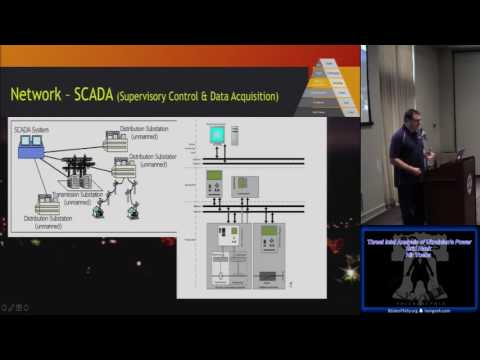
Threat Intel Analysis of Ukrainians Power Grid Hack
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Threat Intelligence
#Security Policies
#Engineering
#Electrical Engineering
#Embedded Systems
#Firmware Development
#Incident Response
#Incident Analysis
0:00 / 0:00