Description:
Explore a Black Hat conference talk that delves into the scenario of an attacker compromising air-gapped industrial control systems (ICS) and SCADA networks using autonomous malware. Learn about reconnaissance techniques used to discover network topology, identify specific industrial devices, and potentially extract sensitive intellectual property. Understand the intricacies of programmable logic controllers (PLCs), including PLC blocks, leather logic, and frequency manipulation. Discover various attack vectors, data exfiltration methods, and detection techniques. Examine the impact of power surges, PLC modes, and CPU utilization on these systems. Investigate passive monitoring, reverse engineering, and the challenges of outdated software in ICS/SCADA environments. Gain insights into the potential vulnerabilities of critical infrastructure and the sophisticated methods employed by threat actors targeting air-gapped networks.
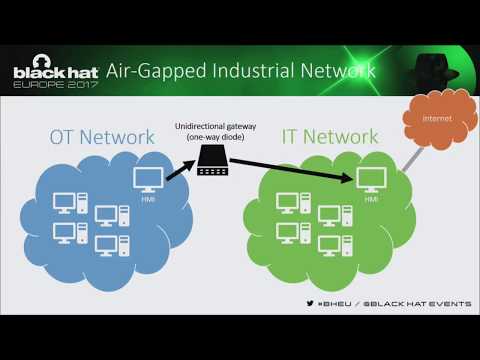
Exfiltrating Reconnaissance Data from Air-Gapped ICS - SCADA Networks
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#SCADA
#Industrial Control Systems Security