Description:
Explore a comprehensive conference talk on building an effective anti-social engineering awareness program. Discover how to transform employees from potential security vulnerabilities into powerful assets against cyber threats. Learn about the speaker's journey from skepticism to developing a successful approach backed by social psychology and behavioral science. Gain insights into strategies that draw parallels between surviving real-world dangers and navigating the digital landscape. Uncover the principles behind a program that significantly increases user resilience to modern cyber threats employing social engineering techniques. Delve into practical applications of this approach in high-profile Ukrainian companies facing unique security challenges. Acquire knowledge on implementing fear-based tactics, social incentives, habit formation, and reward systems to enhance cybersecurity awareness. Examine various triggers, sources of awareness, and methods for improving and retesting security consciousness within organizations.
Read more
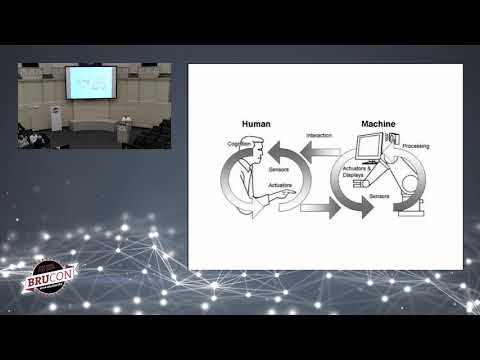
From Weakest Link to Retaliation Weapon - Building Efficient Anti-Social Engineering Awareness Program
Add to list
#Conference Talks
#BruCON
#Information Security (InfoSec)
#Ethical Hacking
#Social Engineering
#Social Sciences
#Behavioral Science
#Psychology
#Social Psychology
#Cybersecurity
#Cybersecurity Awareness
0:00 / 0:00