Description:
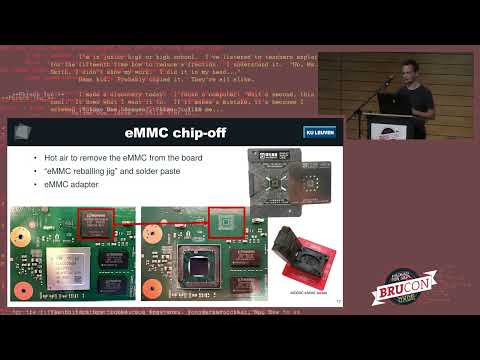
Explore a comprehensive security evaluation of the SpaceX Starlink User Terminal in this BruCON conference talk. Delve into the black-box hardware analysis, uncovering vulnerabilities in the custom quad-core Cortex-A53 System-on-Chip. Learn about the successful bypass of firmware signature verification using voltage fault injection, leading to an unfixable compromise of the terminal. Discover the process of extracting the ROM bootloader and eFuse memory, and understand how the fault model used in countermeasure development falls short in practice. Follow the journey from laboratory experiments to the creation of a custom 'modchip' for executing arbitrary code. Gain insights into the initial exploration of the Starlink network and communication links. The presentation covers various aspects, including hardware revisions, PCB overview, RF components, eMMC extraction, fault injection techniques, and network exploration. Understand the implications of these findings for satellite communication security and the potential for further research in the Starlink ecosystem.
Read more
A Black-Box Security Evaluation of the SpaceX Starlink User Terminal
Add to list
#Conference Talks
#BruCON
#Engineering
#Electrical Engineering
#Embedded Systems
#Firmware Analysis
#Information Security (InfoSec)
#Cybersecurity
#Computer Security
#Hardware Vulnerabilities
0:00 / 0:00